The last five years have seen a dramatic increase in cyber crime, punctuated by some of the most sensational and costly breaches in corporate history. This cyber crime explosion has in turn fueled a spending boom in cybersecurity .
But a practical and effective
cybersecurity strategy
begins with the realization that not every application or data asset requires the same type or level of protection. BCG’s Cyber Doppler tool builds on this insight, enabling companies to better understand their cyber risks and controls. It quantifies the likelihood of a cyber attack occurring as well as the impact of a successful attack.
The Threat of Cyber Crime Is Growing…
In 2017, an attack by the NotPetya virus affected more than 7,000 companies. In its wake, the virus denied access to systems that the Danish shipping giant A.P. Møller-Maersk used to operate shipping terminals worldwide. The problem took two weeks to unsnarl, and cost the company some $200 million to $300 million.
In 2016, hackers issued 35 “orders” via the SWIFT network to withdraw nearly $1 billion from the central bank of Bangladesh’s account at the Federal Reserve Bank of New York. Five of these were carried out, transferring $20 million traced to Sri Lanka and $81 million to the Philippines.
These attention-getting feats represent only the tip of the cyber crime iceberg. The US Federal Bureau of Investigation reports that it received more than 1.4 million complaints of internet crime in the five-year period ending in 2017, representing some $5.5 billion in total losses. In 2018 alone, Symantec recorded a 56% rise in web attacks, a 12% rise in enterprise ransomware attacks, and a 78% rise in supply chain attacks, among other cyber crimes. As these events suggests, the variety of cyber attack methods and ease of committing an attack are on the rise.
The greatest impact may come from the cumulative effect of these thousands of smaller attacks rather than the few spectacular crimes like the Maersk interruption, making the challenge of detecting, preventing, and mitigating them all the greater for their targets. The dark net, where much of cyber crime is incubated, has become so sophisticated that vendors sell their criminal wares through a portal similar to Amazon.com. The portal is complete with user ratings, and it readily accepts a wide range of cryptocurrencies at the click of a button, placing resources for launching attacks in the hands of a multitude of would-be criminals.
…And So, Consequently, Is Cybersecurity Spending
The cyber crime explosion is fueling a cybersecurity spending boom. Companies are purchasing and deploying a plethora of security resources and tools to identify these threats, protect against them, and recover quickly with minimal damage—financial or reputational. Gartner reports that average annual security spending per employee has doubled, from $584 in 2012 to $1,178 in 2018.
When it comes to budgeting cybersecurity, companies typically base decisions on how much they invest relative to their peers, how much they need to spend to close specific gaps, or how much more they need to spend than last year. What they tend not to focus on is any evaluation of the effectiveness of their investment.
The capacity of companies to throw money at the problem of cyber crime is of course limited. Yet even a statement that a company is reducing its cybersecurity spending could itself provoke targeting by hackers. The seemingly infinite variety of cybersecurity products and services to choose from doesn’t make the job of selecting where and how to invest one's cybersecurity any easier.
Seven Strategic Fault Lines
Historically, companies across industries have been prone to make decisions about cybersecurity on the basis of fear after an especially damaging breach or theft—without considering the trade-offs involved. Complicating their decision-making are two realities: cyber attack prevention is expensive and it’s often ineffectual, since businesses can’t know if, when, and how an attack might occur.
To overcome these challenges, companies need to take a step back to better understand their control framework and organizational challenges in detail, and then consider which remediations will give them the best outcomes. They need to know which set of initiatives to invest in and how best to choose between competing projects. And they need to accomplish all this while attacks are constantly and rapidly evolving.
For cybersecurity as for any other threat, companies need to be able to effectively quantify the risk itself, the return on investment from addressing it, and why it may be superior to the return on other projects competing for the same resources. Certainly, chief information security officers (CISOs) would like to invest everywhere they see a threat, observe a gap, and can formulate a potential remedy. But they are forced to make trade-offs based on either their business judgment or a prescribed set of rules.
We’ve identified seven fault lines that impede companies’ strategic thinking and ability to effectively allocate their cybersecurity investment.
Limited insight into key IT assets, threats, and the control framework
Companies often lack a defined process for assessing cyber risk or understanding threats and how these might manifest—such as through unpatched vulnerabilities on phones. Insights into the company’s control framework are often limited as well, with knowledge scattered across the organization and the actual status of controls not documented. Many companies rely on newsletters and updates from security vendors rather than performing regular, independent investigations into the areas where they may be most vulnerable.
Failure to prioritize cybersecurity
Except when a material breach pushes cyber risk to the top of the C-suite’s agenda, cybersecurity and the CISO tend to occupy a peripheral position, disconnected from IT product development, digitization, and operations.
A focus on identification and prevention over detection and response
Security measures are useful mainly in protecting against untargeted attacks. Given the practical impossibility of achieving impermeability from determined assailants, however, reliable information security must also include detection and response. Yet, these processes are often missing from companies’ risk-management frameworks.
Failure to hire talent
The knowledge necessary to tackle threats and sustain operational capabilities is scarce, and companies often struggle to attract and retain needed talent.
Weak third-party management
Companies are increasingly outsourcing the acquisition and management of IT assets and cost control and integrating third-party tools into their digital ecosystems. Yet many don’t know how their IT partners work. And few have the systems, resources, and protocols to oversee and monitor the work of those vendors.
Lack of a security-aware culture
Companies need a culture in which the institution as a whole—not just its risk owners, risk managers, and audit function—takes responsibility for reducing information-security risk, encourages collaboration, and builds systemic resilience . Often, however, systematic accountability from the board to the front lines is missing or poor and sole responsibility for information security falls on the CISO.
Operational stress
As attacks and incidents accelerate, organizational capabilities come under extreme pressure, often leading to systemic breakdowns and accumulating backlogs. Among the culprits: limited knowledge resources; lack of codified incident management processes; insufficient technology to monitor, log, and react to suspicious activity; and an inability to integrate technology and human capabilities.
Assessing the Likelihood of an Attack
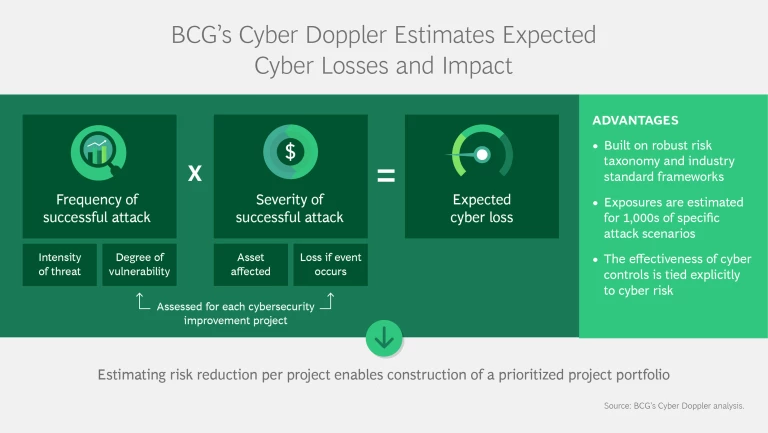
The path to formulating a practical and effective cybersecurity strategy that makes the best use of the company’s investment begins with the realization that not every application or data asset requires the same type or level of protection. Cyber Doppler is a systematic, cutting-edge methodology, model, and software tool developed by a multidisciplinary team at BCG to build on this insight. Leveraging industry-standard cybersecurity and risk-management frameworks, it enables companies to better understand their cyber risks and controls .
Knowing its likely adversaries enables a company to model a comprehensive set of base scenarios that predict outcomes based on the possible actors involved. With Cyber Doppler, the company can quantify the likelihood of a cyber attack occurring as well as the impact of a successful attack on one or more of its assets. That’s because it defines a range of cyber-threat scenarios, assesses them against the control framework, and estimates the likelihood of a breach occurring under each scenario. It then measures the financial impact if an event were to occur across a given set of data, software, and physical assets within a particular region. Cyber Doppler then categorizes and prioritizes assets according to their level of criticality—that is, their financial impact—a process it reruns periodically.
Most cyber criminals fall into a small, finite set of categories. These include nation-states, financial criminals, hacktivists, and even company employees pursuing a finite set of objectives and outcomes such as financial gain, intellectual property theft, disruption of the business, and modification or publication of data.
Cyber Doppler created its attack scenarios based on well-known data breaches—such as NotPetya, Bangladesh Bank, and Edward Snowden’s theft of classified materials from the National Security Agency. The financial impact in these situations was tied directly to the breach event—for instance, lost revenues and regulatory fines —and also included reputational damage to the company. Cyber Doppler consolidates the potential impact across all scenarios to quantify a company’s cyber risk exposure in financial terms.
Threat intensity ebbs and flows depending on the attacker’s resources and mode of operation. For instance, a nation-state deliberately targeting a company would have the resources to pose a more serious breach than a hacktivist might. Cyber Doppler incorporates a threat intensity factor that enables the company to anticipate any increase or decrease in external threat activity. It can also anticipate obsolescence that reduces control effectiveness with the passage of time, all other factors remaining constant, and the cost of maintaining and ensuring robustness of control software and management performance.
Taking Control of Cyber Risk
With resources increasingly strained, it’s more important than ever to maximize return on those that remain. Estimating the expected loss from cyber threats prior to and following a given set of interventions—such as a cybersecurity improvement project—enables a company to estimate loss reduction per project and construct an optimized project portfolio. This analysis ensures that the company can earn the maximum return on its cyber investment.
Cyber Doppler also lets companies consider carefully which controls drive the most value in a loss-distribution estimation approach. This analysis enables better, more informed discussions about cyber risk protection.