Many organizations are unprepared to protect themselves against geopolitically motivated attacks. It’s time to recognize the risks and start planning a strong defense.
Cyber wars are no longer the realm of fantasy; they are becoming a reality—and one frequently waged by surrogates, which makes them murky affairs. The relationship between the surrogates and their sponsor nation-states is often ambiguous, as are the underlying motivations for the attacks. What’s clear is that private organizations of all sizes and types are potential targets in a high-stakes board game and that they need a new mindset to protect themselves against increasing cybersecurity risks.
Cyber attacks are not new in geopolitics, but their frequency is rising.
Cyber attacks are not new in geopolitics, but their frequency is rising, the damage more devastating, the targets more varied, and the motivations more far-reaching. Increasingly, cyber warfare is not simply conducted between nations. The targets are often companies, private networks, and infrastructure. Recently, water systems, hospitals, and other critical infrastructure such as pipelines have experienced attacks linked to state actors. These types of attacks accelerated during the pandemic as hackers took advantage of the vulnerabilities of remote work , and concerns over this type of warfare have mounted since the start of the war in Ukraine.
Historically, nations initiated cyber attacks to gather intelligence. Recently, such attacks appear to have expanded in scope, disrupting services and businesses seemingly with the goal of weakening society.
At the same time, the boundaries between traditional organized crime and geopolitical crime are blurring. A single individual, operating in secret, can cripple vital national infrastructure or an unsuspecting and unprepared company.
Many organizations are unprepared to protect themselves in this increasingly hostile, asymmetrical, and secretive world. They have not yet internalized the need to harden their defenses as the new age casts a dark, murky shadow over the private sector. Is your organization prepared?
What Does This Mean for Organizations?
The expanding threat posed by cyber attacks has at least three implications for companies, even those whose businesses would not historically make them geopolitical targets.
Everyone Is Exposed
Even small and midsize enterprises such as regional hospitals have been victims of cyber attacks. Increasingly, hackers are infecting open-source software widely used by organizations of all sizes. Case in point: in December 2021, a computer bug infected a popular open-source tool, Log4j, that tracks computer activity. Bad actors quickly began using the tool to take control of or infect computer systems. A senior US cybersecurity official called it “one of the most serious vulnerabilities I have seen.”
Organizations Must Prepare for Attacks with Different Motivations
When the motives behind attacks expand into the geopolitical realm, preparation and risk management become more complex. Organizations are now fending off attacks designed to harm or inconvenience civilians or sow discord. Attacks against websites, disruptions of service, and the creation and distribution of fake news all fit the bill.
The Weapons Are Increasingly Advanced
Organizations must be constantly on guard as the tools of the hacking trade are becoming increasingly sophisticated and more widely available. In a spiraling arms race, nations and nonstate actors alike are developing more powerful weapons, which in turn encourage the development of stronger cyber shields, which encourage the development of stronger weapons, and so on.
In this treacherous setting, preparation is essential.
Risk and Crisis Management Readiness
The days of treating cybersecurity as an afterthought or an add-on are long over. Organizations need a full suite of capabilities to keep attacks at bay. They have two primary sets of activities: identifying and mitigating the risks and ensuring that the organization is ready if a hack occurs.
The days of treating cybersecurity as an afterthought or an add-on are long over.
Identifying and Mitigating the Risks
Organizations need to treat cyber risk as an existential business threat. They need to build layers of surveillance, preparation, and protection.
Put cyber risk in the C-suite. In an increasingly hostile world, cybersecurity belongs in the C-suite. Too many organizations continue to assign sole responsibility for managing this risk to the IT department or chief information security officer. Unless the topic is in the C-suite, cybersecurity will exist apart from business and strategy rather than being tightly integrated with them.
Quantify the cyber risk exposure. Cyber risk is inherently unpredictable and uneven but not uncertain. All but the smallest or luckiest of businesses will likely come under attack. As with most other certain risks, organizations should quantify their exposures to cyber attacks and anticipate the costs and resources required to combat them. This quantification should be ongoing and dynamic because cyber risks change over time.
Plan for various threat scenarios. In the risk assessment process, organizations should evaluate threat scenarios in which the attacker is a nation-state or the hacks are motivated by geopolitics. These scenarios need to be incorporated into the final decision making on cybersecurity investments.
The SolarWinds hack in 2020, an attack widely thought to have been undertaken for geopolitical reasons, can serve as an example of how to assess threat scenarios.
A scenario-planning exercise focused on cyber threats should explore the answers to four questions:
- Who might attack?
- Why—what would motivate the attackers?
- Where might they strike?
- How would the hack be carried out (the potential forms of attack)?
Now that nation-states may be the “who” and geopolitical motivations may be the “why,” the stakes are higher for all organizations. They need to invest in cybersecurity mitigation that can address the expanded set of scenarios rather than dismissing them as highly unlikely. (See Exhibit 1.)
Be better than others. In geopolitical attacks, actors are often scanning the landscape for the weakest target. If the goal is to wreak havoc, actors may be less concerned with which organization they attack. A business with stronger capabilities than its peers, even if it is not best-in-class, might avoid being compromised. Organizations should be continually upgrading their capabilities so that they stay ahead of the pack.
Manage the supply chain risks.
Supply chains
are a prime target of geopolitical attacks because successful hacks can almost bring down an entire sector. The objective of a typical supply chain cyber attack has historically been espionage or disruption. These strikes tend to be sophisticated and resourceful. The risks of cyber attacks on supply chains are varied but include disruptions related to:
- A technology vendor being compromised
- A supplier suffering an outage from a cyber attack
- Ransomware or a kind of backdoor being inserted into software purchased from a vendor
- A data breach occurring after a data-processing provider suffers an attack
In 2020 and 2021, news organizations and companies themselves reported on several such attacks. Accellion, a file-sharing and collaboration vendor, reported that attackers exploited its file transfer software allowing access to customer data stored on the cloud. Kaseya, a provider of software for remote IT monitoring and management, experienced a breach in July 2021. Attackers were able to remotely deploy ransomware on the networks of Kaseya’s customers. As a result, the Swedish retailer Coop was forced to shut at least 800 stores for a day.
Increasingly, the hackers behind these attacks are persistent, highly skilled actors backed either by nation-states or by large, well-financed cybercriminal groups. Of the more than 24 high-impact global supply chain cyber attacks reported from January 2020 through July 2021, more than half were perpetrated by well-known “advanced persistent-threat” groups, often believed to be backed by nation-states.
Being Ready When an Attack Occurs
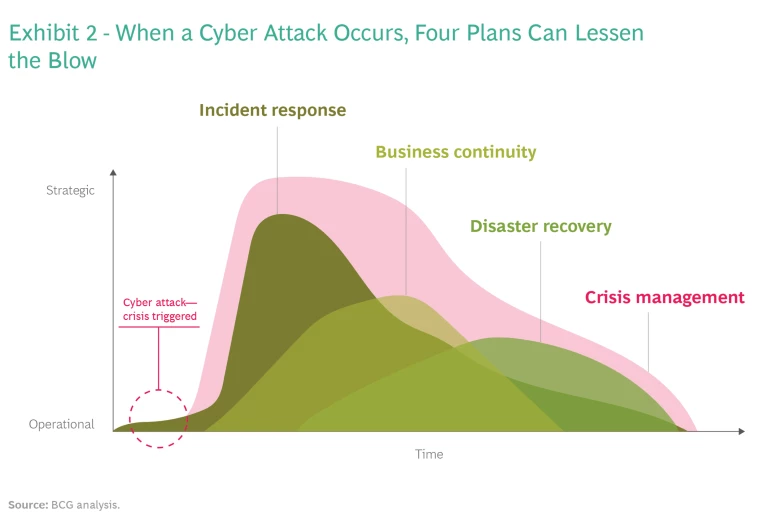
In today’s perilous world, prevention is not always possible. Eventually, many organizations will suffer an attack. The effectiveness of their response will hinge on their pragmatism, preparedness, and resilience. Companies should have four types of plan to combat an attack (see Exhibit 2):
- Incident Response. The steps to prepare for, detect, contain, and recover from an attack.
- Business Continuity. A plan for how the organization will keep operating while recovering from the attack.
- Disaster Recovery. A step-by-step guide for returning to a preattack state.
- Crisis Management. A comprehensive outline of the legal, regulatory, financial, and communication activities and decision rights required to manage through the crisis.
In addition, organizations should establish ongoing communication and dialogue with the leading national agencies and authorities that can provide assistance. When a hack is rooted in geopolitics, regulators and other public bodies can be indispensable.
Being a good neighbor is also part of organizational readiness. If a company is hacked and the attack is spreading, the organization can help others minimize their exposure by sharing indicators of compromise such as forensic evidence of intrusion.
One of the best ways to be ready is to practice. Buildings routinely run fire drills to prepare residents in the event of an emergency. Businesses should conduct similar tabletop exercises so that boards of directors, C-level executives, and employees understand what might happen in a cyber attack and the steps that they should take. The more comprehensive and tested the plan, the better the organization’s response to an incident will be.
These exercises pay dividends in the real world. During a real fire, you don’t want to be trying to find the exits.
Since 2016, NATO has recognized cyberspace as a theater every bit as critical as land, sea, and air to the defense of its member countries. At the Brussels summit in 2021, NATO members endorsed a new policy recognizing the need for collective defense, crisis management, and cooperation in combating cyber threats.
As recent history has shown, these attacks are often targeted at privately owned infrastructure. It’s time for all businesses to take these threats as seriously as NATO.