Chief information security officers face a continually evolving challenge. The threat landscape is changing all the time, requiring unrelenting vigilance. Yet even as CISOs seek to enhance their company’s security posture, they must deal with talent shortages and competing budget priorities. To better understand these issues, BCG recently partnered with GLG, a research firm that primarily serves the financial industry, to survey more than 350
cybersecurity
leaders from companies around the world.
Key takeaways from our analysis include the following:
- Overall, cyber maturity is growing—especially in areas like cybersecurity governance, risk, and compliance—but gaps remain.
- CISOs are worried about growing threats but also about controlling spending.
- Cyber-mature organizations distinguish themselves in unglamorous but important ways like governance and coordination among IT, business, and cybersecurity.
- AI-enabled threats are no longer hypothetical; the majority of CISOs have faced AI-powered phishing and malware attacks, and most CISOs are eager to use
AI
in fighting back.
- Although most CISOs say they want to reduce their vendor count, the real story is much more nuanced, with many continuing to expand in select segments.
These findings offer critical insights for cybersecurity executives, investors (including PE firms), and vendors.
Cyber Maturity Is Growing
In our survey, companies assessed themselves on how effectively they have adopted 12 best practices in cybersecurity, from data protection to incident response and third-party cyber risk management. Overall, company scores increased across most of the 12 areas from 2023 to 2024, indicating that cyber maturity is growing. The biggest gains were in cybersecurity governance, risk, and compliance (an increase of 8 percentage points), driven by growing regulatory pressures and an increased awareness of the importance of internal governance practices. Business continuity and resilience scores also increased, up 8 percentage points.
Despite this progress, some critical gaps remain. For example, only 25% of companies achieved the highest score for app security, and only 22% did so in data protection or software supply chain risk management. (See Exhibit 1.) Third-party cyber risk management is also a core priority, but just 28% of companies achieved the highest score.
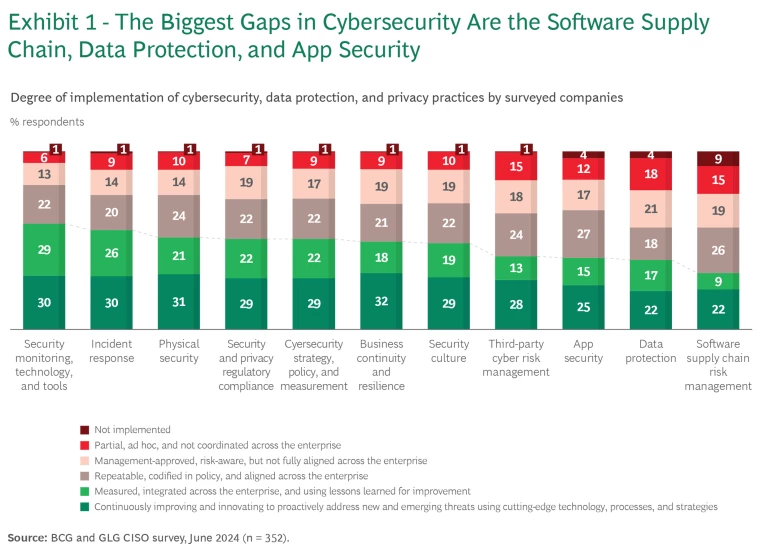
Among the biggest barriers to improved cybersecurity are talent shortages (cited by 59% of CISOs, more than any other factor), insufficient budgets (53%), and competing IT priorities (46%).
Shifting Priorities in an Ever-Changing Cyber Landscape
The range of cyber threats is growing, and their frequency is increasing. Among the greatest concerns for the CISOs in our survey are the rising frequency of known threats such as ransomware (cited as critical by 81% of respondents), ensuring that risk mitigation keeps pace with tech innovation (74%), and the increasingly complex landscape of cyber and privacy regulations (67%).
Lower on the list of priorities is controlling cyber spending (54%). This disparity—with growing threats a bigger concern than controlling spending—holds true across most industries. (See Exhibit 2.)
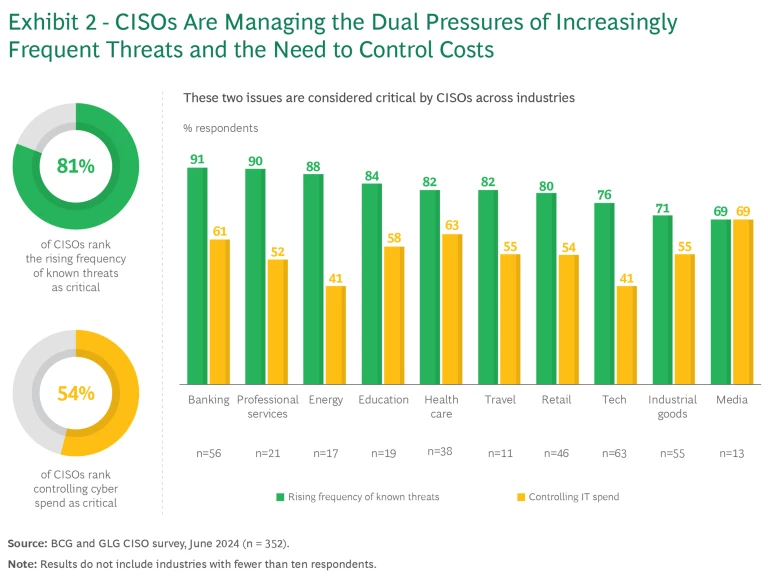
Although every organization is different, overall spending levels are growing, with 76% of respondents expecting an increase in cybersecurity spend this year. Moreover, that growth is accelerating; respondents estimated that their cyber spending increased by 9% in 2023 and will increase by 11% this year. (Spending estimates for Asia-Pacific companies were higher than for companies in North America and Europe.)
When asked to pick three products they expected to see the largest spend increase in, companies reported:
- Zero-trust network access (cited in the top three by 21% of respondents)
- Identity and access management (cited in the top three by 17% of respondents)
- Cloud security posture management (cited in the top three by 14% of respondents)
- Data security (cited in the top three by 13% of respondents)
But spending more does not correlate with greater cyber maturity. Nearly half of the least mature organizations in our survey allocate more than 10% of their IT spend to cyber. These companies may be throwing money at the problem, instead of investing strategically. They may also be paying the price—literally—for sticking with outdated IT systems, or trying to play catch-up after years of underinvestment.
Conversely, 40% to 45% of highly cyber-mature organizations allocate less than 10% of their IT spending to cyber. Many of these companies are “spending smart”—and capitalizing on previous wise cyber investments. Some are also reaping benefits from creating a modern, consolidated IT environment. Advanced companies are far more likely than unprepared firms to measure cyber investment ROI systematically.
How Cyber-Mature Organizations Set Themselves Apart
We segmented companies into five tiers based on their level of cyber maturity (recall Exhibit 1 above) and identified a number of features that separate cyber-mature organizations from the rest of the pack:
- Accountability. For organizations in the top two (“advanced” and “proactive”) tiers of performance, CISOs are more likely than other stakeholders, such as product owners or business units, to be directly accountable for aspects of cybersecurity. At these companies, CISOs and tech leaders own the cybersecurity agenda, and that accountability leads to a greater likelihood that broad and smartly targeted defensive measures will be implemented.
- Coordinating IT Recovery and Business Continuity. Among high-maturity organizations, more than 80% combine business processes and IT asset recovery priorities when planning recovery from an enterprise-wide cyber event.
- Centralized Decision Making. Cyber-mature organizations are characterized by more centralized decision making regarding cyber solutions. For example, about 10% more organizations in the top-performing tier centrally manage functions like app security testing and product security within the CISO team. Among less mature companies, those decisions are typically made by product teams.
AI Poses a New Threat—and a Potential Solution
A major theme in the survey responses was the increasing prevalence of AI. Among specific threats, AI-enabled social engineering (such as phishing attacks) was cited as the top concern, considered either a significant or a critical issue to address over the next 12 months by 57% of CISOs. That was followed by AI-enabled malware (52%) and AI-enabled fraud (49%). Regulatory challenges, privacy, and other factors were all further down in the threat rankings. (See Exhibit 3.)
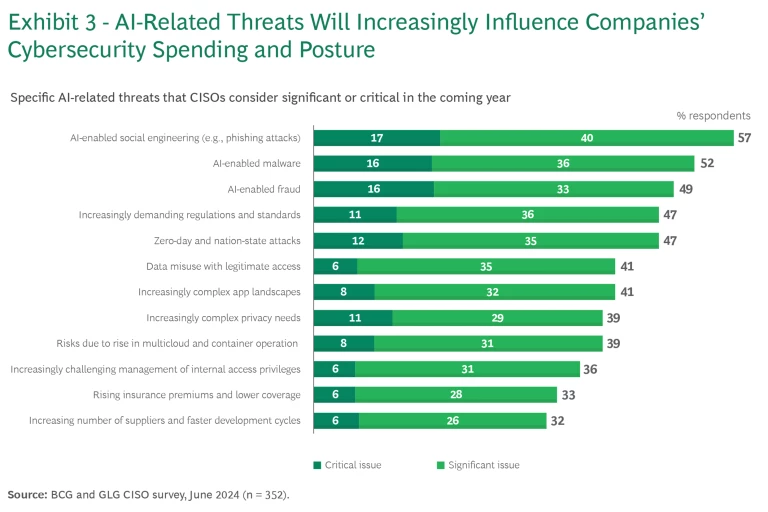
CISOs also noted that AI and GenAI could increase the cyber threat in other areas, including data security, identity and access management, and application security. All were cited by 35% to 45% of CISOs as categories of cyber products that need enhancements to address GenAI-related threats.
Notably, the survey also showed that AI (including GenAI) is no longer a hypothetical threat. Among respondents, 38% have experienced at least one attack using AI- or GenAI-powered malicious code generation in the past 12 months. The numbers are even greater for malware embedded with AI (59%) and AI-enhanced automated phishing attacks (72%).
At the same time, GenAI poses a potential solution to some of these problems, reflecting the arms race nature of cybersecurity. Cybersecurity vendors are starting to incorporate GenAI into their products, and CISOs are receptive.
- 75% expressed some degree of openness and comfort with exploring GenAI-powered solutions.
- More than 60% of CISOs would prefer to purchase GenAI solutions from existing cyber vendors, rather than from new players or specialists.
- 18% are already using GenAI-powered cyber solutions or are in the process of implementing them.
- CISOs are willing to pay a premium of approximately 10% for GenAI-enabled solutions—especially those who are already implementing or who plan to implement such solutions.
These trends suggest an emerging opportunity for cybersecurity vendors.
CISOs Want to Reduce Their Vendor Count
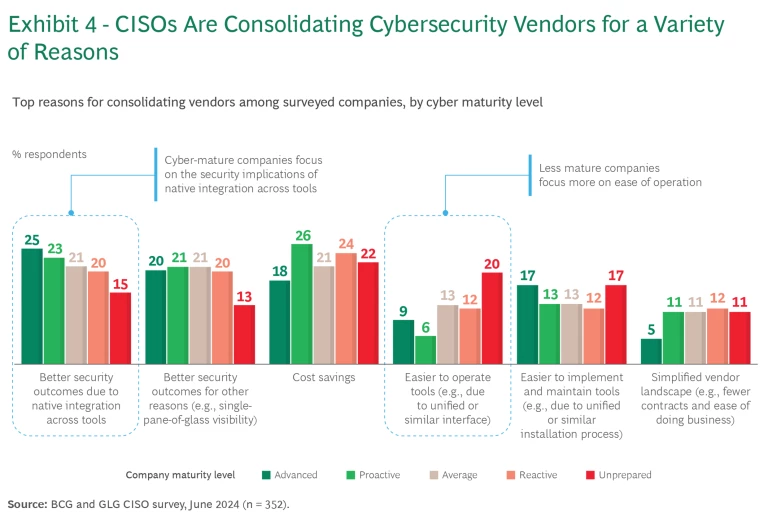
Our previous survey in 2023 showed that companies were seeking to consolidate their cybersecurity vendors, and the results for 2024 show that trend has accelerated. Across most product categories, more respondents plan to consolidate their vendor base than expand it. The difference is particularly stark in areas such as firewall and network detection and response, with a net difference of 15 percentage points in favor of consolidation.
The primary reason? CISOs cite better security outcomes, followed by cost savings and a desire to simplify vendor implementation and management. Moreover, the rationale for consolidating vendors varies by maturity level. More-mature companies focus on the security implications of native integration across tools. In contrast, less mature companies tend to prioritize cost savings, ease of operations, and ease of implementing and maintaining tools. (See Exhibit 4.)
The Bottom Line for Stakeholders
Our analysis suggests several priorities for stakeholders.
Priorities for CISOs. First, CISOs must increase their focus on cyber governance and compliance, business continuity, and identification of threats along the software supply chain. The central CISO team should play a bigger role in planning the overall cyber posture of the enterprise, including tech usage, support for business units, risk and compliance , and oversight of digital-product teams.
Priorities for Investors. Private equity firms with investments in cybersecurity vendors should push companies to develop more advanced, comprehensive solutions in order to capitalize on the trend toward vendor rationalization. Providers should also seek to integrate GenAI into their products, and they can consider service offerings to support CISOs in dealing with cyber talent shortages and competing IT priorities.
Building out the portfolio in this way requires investment, so firms should assess potential disruptions to the competitive landscape—particularly among large platform players like Microsoft—before making bold bets.
Priorities for Cybersecurity Vendors. Vendors need to continue building out their offerings by improving capabilities and incorporating GenAI. In addition, they need to revamp their marketing to educate customers and reinforce the ways that their products are better positioned than those of competitors. Armed with the knowledge that CISOs are seeking to consolidate vendors, cybersecurity providers should emphasize the simplicity of using a single vendor—while also shoring up their defenses so that customers are not overly exposed to a single vendor.
Cybersecurity requires relentless vigilance—but it also requires strategic effort and investment. The insights gained from our survey can help CISOs, investors, and vendors understand the changing threat landscape and the steps they can take to succeed.
The authors thank their BCG colleagues Geno Quaid, Morgan Romey, and Renae Tamura for contributions to this article.














